Can you trust your computer? Three ways your system may already be unsafe
08.16.2022
We invest in a "reliable" computer/technology brand, purchase one or more top-rated cyber-protective tools and assume our personal information is protected. But, what we don't realize is that even before we do ANY of this, our computer may already be compromised. A compromised computer may crash more often but it can also open backdoors leading to identify theft, cyberattacks, espionage, sabotage, operational failure and safety hazards. Here are three things that can happen in the supply chain that may result in a faulty computer.
1. The Silicon was Altered
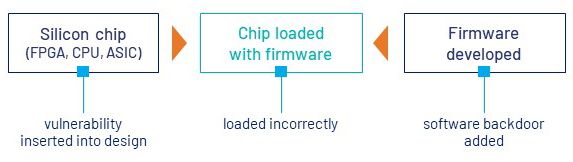
- What can go wrong: Chips may be designed in the U.S., but they are mostly manufactured abroad – currently the largest semiconductor manufacturer is in Taiwan. Offshore supply chain dependency and counterfeit chips are a growing concern and there is a chance that malicious insiders can insert vulnerabilities into chip designs and add firmware backdoors. Even when manufactured in a more secure facility, firmware can be loaded incorrectly, which can jeopardize security.
- Preventive measures: Perhaps the most recent preventive development in the USA is the proposed CHIPS Act, which seeks to reduce counterfeits and supply chain dependency with $52 billion in incentives to encourage semiconductor manufacturing in the United States. In fact, technology leader Intel® is investing $20 billion in new manufacturing factories in Arizona in addition to their existing supply chain transparency efforts. Quality assurance procedures can detect unauthorized design changes, and loading signed and authenticated firmware in secure, trusted facilities can prevent backdoors. Designers can also use physically unclonable function (PUF) technology to create digital silicon fingerprints that prevent system tampering.
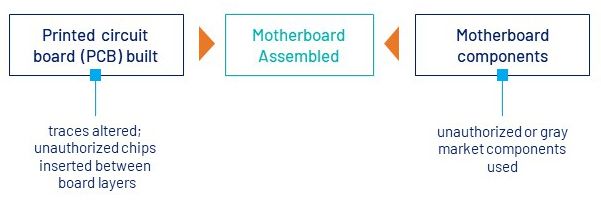
- What can go wrong: An insider can alter traces and chips between PCB layers and use unauthorized or counterfeit components to create backdoors. A disputed but alarming Bloomberg article claimed malicious chips had been inserted on Supermicro motherboards during the manufacturing process, enabling network data from the Department of Defense to be sent to China.
- Preventive measures: Motherboards designed, built and tested in the USA by trusted IPC-1791 certified manufacturers mitigate insider threats and counterfeits through supply chain management, testing and physical security measures.
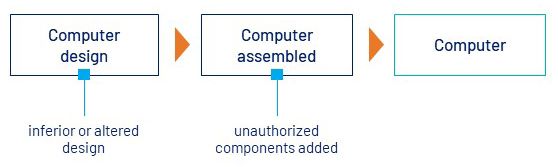
- What can go wrong: Unauthorized components and altered computer or subsystem designs can decrease system reliability, performance and longevity.
- Preventive measures: Design assurance tests and anti-tamper technologies confirm systems are built correctly and safeguard systems against reverse engineering. Company cybersecurity policies and insider threat programs are essential for preventing unauthorized disclosure or leakage of sensitive design material and destructive individual behavior.
2. The Motherboard was Changed
3. It was Assembled Incorrectly
Innovative technology is only as good as its supply chain
Even the most innovative computer can become a liability if it is built utilizing a questionable supply chain without stringent regulations, policies, procedures and management. Next time you buy a computer, ask the manufacturer what they do to ensure supply chain integrity. You may be surprised by the answer.



